While October is designated the official Cybersecurity Awareness Month, we believe every day should be treated as cybersecurity awareness day! Here are the top 5 areas you need to focus on TODAY to strengthen your cybersecurity framework against cybercrime.
What is cybercrime?
Cybercrime is usually committed by hackers who want to make money. It can be carried out by an individual or an entire underground operation and can vary with the level of sophistication. However, there are certain instances where cybercrime will be committed for other reasons, such as a disgruntled employee (this is less common, but still a threat).
Yeah, but they’re only attacking big business, right?
Wrong. This is a common misconception likely fueled by the vast amounts of attention that larger corporations receive when a breach occurs, but small and medium-sized businesses are just as vulnerable as larger ones. They are less likely to have the security systems in place to prevent and detect an attack and also less likely to recover from an attack without paying the ransom or fee demanded of them.
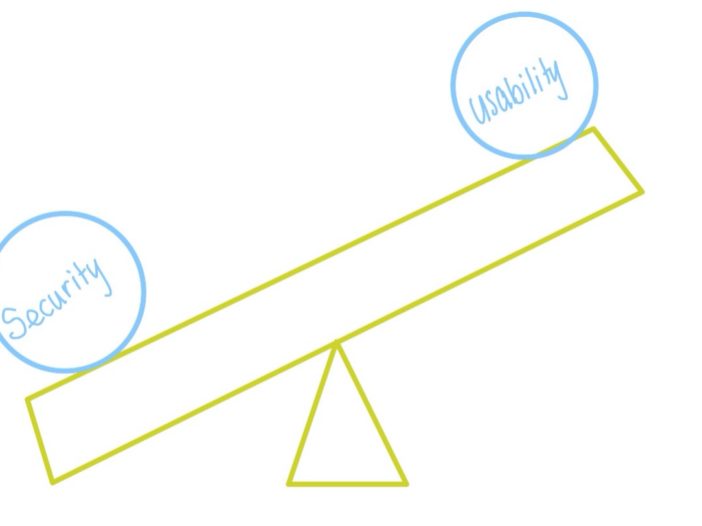
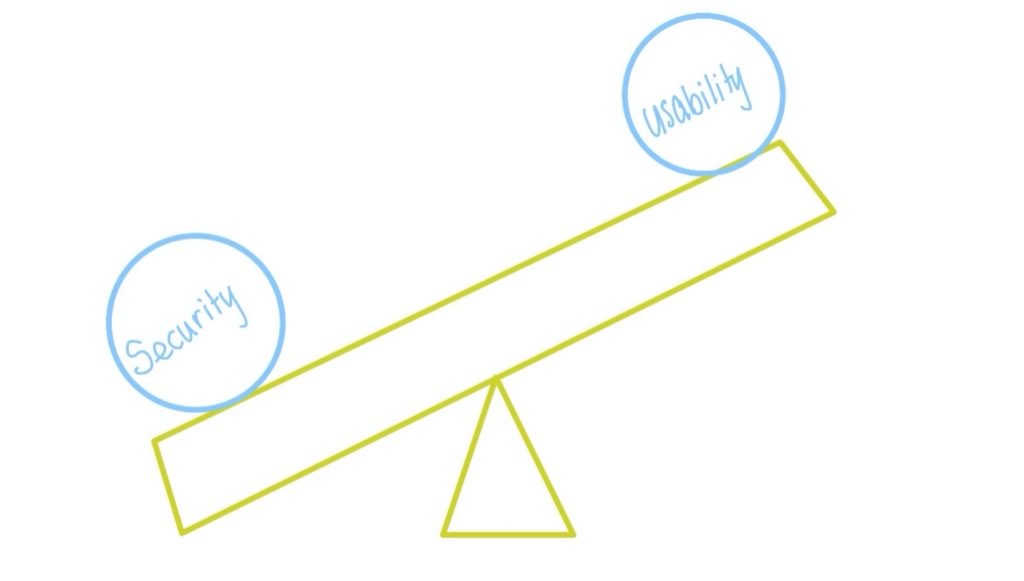
It’s important to note that we cannot 100% prevent a breach from occurring and proper security protocols need to weigh both the usability for employees and the security of the organization. As you increase security, the usability drops so it’s very much a balancing act. The most secure computer in the world is one that’s unplugged from the power – but you won’t be able to do much with it, right?
The top 5 cybersecurity framework areas to focus on:
1. Bring Your Own Device (BYOD) Policy
In our work-from-home environment that still promotes team collaboration, more organizations than ever are allowing employees to work on their own devices. This could be anything from using a personal cell phone to access company email to a personal laptop or tablet to access company resources. And while this is great, it’s very important for you to evaluate several key things including what would happen to your organization if that device was lost, stolen, or breached.
A BYOD policy outlines how employees can use their device to access company resources (if at all) and is used to enforce the Mobile Device Management (MDM) that will be used to protect your organizational resources. It will have several key things in it including the ability to grant access to sensitive data only through trusted networks, encrypting data on the device to prevent unauthorized access, enforcing strong password policies, and the ability to remote wipe company resources in the event of a lost device.
A BYOD policy can get complex and there are a lot of moving parts to it so please don’t hesitate to reach out to us if you would like some assistance with getting one enforced.
2. Set Security Standards Using Multi-Factor Authentication & Strong Passwords
It’s very important to look at the passwords that are in use throughout the organization. Are they strong passwords that are stored in a password manager or are they weak passwords that are sitting in a text file on the desktop?
Using a password manager is important to protecting your business because it enables employees to feel comfortable creating more complex passwords. It also makes logging into your company resources a breeze with auto-fill capabilities.
Another important aspect to your passwords is the use of multi-factor authentication (MFA). Someone could have your password and be able to authenticate that way but the 2nd factor (usually a text sent to your phone or a push notification to an app on your phone) will stop them from getting through.
3. Disaster Recovery (DR) Plan
Building a solid DR Plan is paramount to your organization surviving a cyber-attack. This is because you will be planning for important details such as backing up your critical IT systems, testing the backups on a regular basis, evaluating your goals in the event of a disaster, and what IT assets will be involved.
4. Staff Training
Training your staff on the best way to spot phishing attempts and to be more cautious and alert when browsing the internet is another very important task at hand. We want to make sure that everyone in the organization from the executive to the intern are aware of how to stay safe both online and offline and why protecting the organization’s data and security is an important part of their daily responsibilities.
5. Update your Applications Regularly
Regularly updating your applications will help keep the organization’s IT infrastructure more secure. This is because software vendors issue important security updates and patches to their systems on a regular basis. Trying to keep the upper hand on the cyber criminals means software companies are regularly trying to break into their own software and patch it before the criminals get to it.
Get Help From an IT Solutions Partner (H2)
If you’re looking for an IT solutions partner who will walk with you through every step of the way and help assist with making some of these IT decisions, please schedule a call with our team today. We’ll talk you through the options that are available to you and get a full understanding of how your organization operates so that we can make the appropriate recommendations regarding your IT environment and infrastructure.